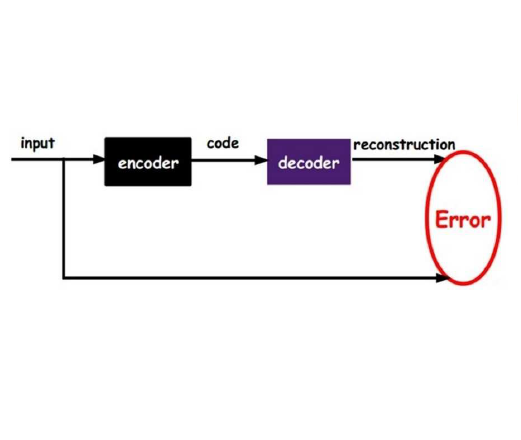
The inclusion of Internet of Things (IoT) devices is growing rapidly in all application domains. Smart Farming supports devices connected, and with the support of Internet, cloud or edge computing infrastructure provide remote control of watering and fertilization, real time monitoring of farm conditions, and provide solutions to more sustainable practices. This could involve using irrigation systems only when the detected soil moisture level is low or stop when the plant reaches a sufficient level of soil moisture content. These improvements to efficiency and ease of use come with added risks to security and privacy. Cyber attacks in large coordinated manner can disrupt economy of agriculture-dependent nations. To the sensors in the system, an attack may appear as anomalous behaviour. In this context, there are possibilities of anomalies generated due to faulty hardware, issues in network connectivity (if present), or simply abrupt changes to the environment due to weather, human accident, or other unforeseen circumstances. To make such systems more secure, it is imperative to detect such data discrepancies, and trigger appropriate mitigation mechanisms. In this paper, we propose an anomaly detection model for Smart Farming using an unsupervised Autoencoder machine learning model. We chose to use an Autoencoder because it encodes and decodes data and attempts to ignore outliers. When it encounters anomalous data the result will be a high reconstruction loss value, signaling that this data was not like the rest. Our model was trained and tested on data collected from our designed greenhouse test-bed. Proposed Autoencoder model based anomaly detection achieved 98.98% and took 262 seconds to train and has a detection time of .0585 seconds.
相關內容
Multiparty computation (MPC) consists in several parties engaging in joint computation in such a way that each party's input and output remain private to that party. Whereas MPC protocols for specific computations have existed since the 1980s, only recently general-purpose compilers have been developed to allow MPC on arbitrary functions. Yet, using today's MPC compilers requires substantial programming effort and skill on the user's side, among other things because nearly all compilers translate the code of the computation into a Boolean or arithmetic circuit. In particular, the circuit representation requires unrolling loops and recursive calls, which forces programmers to (often manually) define loop bounds and hardly use recursion. We present an approach allowing MPC on an arbitrary computation expressed as ordinary code with all functionalities that does not need to be translated into a circuit. Our notion of input and output privacy is predicated on unlinkability. Our method leverages co-utile computation outsourcing using anonymous channels via decentralized reputation, makes a minimalistic use of cryptography and does not require participants to be honest-but-curious: it works as long as participants are rational (self-interested), which may include rationally malicious peers (who become attackers if this is advantageous to them). We present example applications, including e-voting. Our empirical work shows that reputation captures well the behavior of peers and ensures that parties with high reputation obtain correct results.
Cyber-physical systems are infrastructures that use digital information such as network communications and sensor readings to control entities in the physical world. Many cyber-physical systems in airports, hospitals and nuclear power plants are regarded as critical infrastructures since a disruption of its normal functionality can result in negative consequences for the society. In the last few years, some security solutions for cyber-physical systems based on artificial intelligence have been proposed. Nevertheless, knowledge domain is required to properly setup and train artificial intelligence algorithms. Our work proposes a novel anomaly detection framework based on error space reconstruction, where genetic algorithms are used to perform hyperparameter optimization of machine learning methods. The proposed method achieved an F1-score of 87.89% in the SWaT dataset.
Time series data are often corrupted by outliers or other kinds of anomalies. Identifying the anomalous points can be a goal on its own (anomaly detection), or a means to improving performance of other time series tasks (e.g. forecasting). Recent deep-learning-based approaches to anomaly detection and forecasting commonly assume that the proportion of anomalies in the training data is small enough to ignore, and treat the unlabeled data as coming from the nominal data distribution. We present a simple yet effective technique for augmenting existing time series models so that they explicitly account for anomalies in the training data. By augmenting the training data with a latent anomaly indicator variable whose distribution is inferred while training the underlying model using Monte Carlo EM, our method simultaneously infers anomalous points while improving model performance on nominal data. We demonstrate the effectiveness of the approach by combining it with a simple feed-forward forecasting model. We investigate how anomalies in the train set affect the training of forecasting models, which are commonly used for time series anomaly detection, and show that our method improves the training of the model.
Low/No-code development is a software development method that provides users with a platform for visually creating applications with little or no coding. Companies and organizations need software applications and information systems for various business purposes like management in the technology era. Low/No-code development gives non-IT professionals a convenient tool for rapidly building simple business applications they need without or with little coding. In this paper, we explored the benefits & limitations of Low/No-Code development and modern Low/No-Code development platforms in the industry. In addition, we analyzed how it can be improved and prospected the impacts of Low/No-Code development on society and related industries in the future. In conclusion, we find that Low/No-code development is a promising trend that can significantly impact future software development and digital transformation.
To ensure an efficient and environmentally friendly water resource management, water management associations need means for efficient water monitoring as well as novel strategies to reduce the pollution of surface and ground water. Traditionally, water management associations operate large sensor networks to suffice their needs for hydrological and meteorological measurement data to monitor and model physical processes within catchments. Implementing a comprehensive monitoring system often suffers from sparse coverage of in-situ data. Due to the evolvement of the Copernicus satellite platforms, the broader availability of satellite data provides a great potential for deriving complementary information from Earth Observation data. Although the number of satellite data platforms that provide online processing environments is growing, it is still a big challenge to integrate those platforms into traditional workflows of users from environmental domains such as hydrology. Thus, in this paper, we introduce a software architecture to facilitate the generation of Earth Observation information targeted towards hydrology. The presented WaCoDiS System comprises several microservices as well standardized interfaces that enable a platform-independent processing of satellite data. First, we discuss the contribution of Earth Observation data to water monitoring and derive several challenges regarding the facilitation of satellite data processing. We then describe our system design with a brief overview about the different system components which form an automated processing pipeline. The suitability of our system is proven as part of a pre-operational deployment for a German water management association. In addition, we demonstrate how our system is capable of integrating satellite data platforms, using the Copernicus Data and Exploitation Platform - Deutschland (CODE-DE) as a reference example.
The monitoring and management of numerous and diverse time series data at Alibaba Group calls for an effective and scalable time series anomaly detection service. In this paper, we propose RobustTAD, a Robust Time series Anomaly Detection framework by integrating robust seasonal-trend decomposition and convolutional neural network for time series data. The seasonal-trend decomposition can effectively handle complicated patterns in time series, and meanwhile significantly simplifies the architecture of the neural network, which is an encoder-decoder architecture with skip connections. This architecture can effectively capture the multi-scale information from time series, which is very useful in anomaly detection. Due to the limited labeled data in time series anomaly detection, we systematically investigate data augmentation methods in both time and frequency domains. We also introduce label-based weight and value-based weight in the loss function by utilizing the unbalanced nature of the time series anomaly detection problem. Compared with the widely used forecasting-based anomaly detection algorithms, decomposition-based algorithms, traditional statistical algorithms, as well as recent neural network based algorithms, RobustTAD performs significantly better on public benchmark datasets. It is deployed as a public online service and widely adopted in different business scenarios at Alibaba Group.
The prevalence of networked sensors and actuators in many real-world systems such as smart buildings, factories, power plants, and data centers generate substantial amounts of multivariate time series data for these systems. The rich sensor data can be continuously monitored for intrusion events through anomaly detection. However, conventional threshold-based anomaly detection methods are inadequate due to the dynamic complexities of these systems, while supervised machine learning methods are unable to exploit the large amounts of data due to the lack of labeled data. On the other hand, current unsupervised machine learning approaches have not fully exploited the spatial-temporal correlation and other dependencies amongst the multiple variables (sensors/actuators) in the system for detecting anomalies. In this work, we propose an unsupervised multivariate anomaly detection method based on Generative Adversarial Networks (GANs). Instead of treating each data stream independently, our proposed MAD-GAN framework considers the entire variable set concurrently to capture the latent interactions amongst the variables. We also fully exploit both the generator and discriminator produced by the GAN, using a novel anomaly score called DR-score to detect anomalies by discrimination and reconstruction. We have tested our proposed MAD-GAN using two recent datasets collected from real-world CPS: the Secure Water Treatment (SWaT) and the Water Distribution (WADI) datasets. Our experimental results showed that the proposed MAD-GAN is effective in reporting anomalies caused by various cyber-intrusions compared in these complex real-world systems.
With the growth of mobile devices and applications, the number of malicious software, or malware, is rapidly increasing in recent years, which calls for the development of advanced and effective malware detection approaches. Traditional methods such as signature-based ones cannot defend users from an increasing number of new types of malware or rapid malware behavior changes. In this paper, we propose a new Android malware detection approach based on deep learning and static analysis. Instead of using Application Programming Interfaces (APIs) only, we further analyze the source code of Android applications and create their higher-level graphical semantics, which makes it harder for attackers to evade detection. In particular, we use a call graph from method invocations in an Android application to represent the application, and further analyze method attributes to form a structured Program Representation Graph (PRG) with node attributes. Then, we use a graph convolutional network (GCN) to yield a graph representation of the application by embedding the entire graph into a dense vector, and classify whether it is a malware or not. To efficiently train such a graph convolutional network, we propose a batch training scheme that allows multiple heterogeneous graphs to be input as a batch. To the best of our knowledge, this is the first work to use graph representation learning for malware detection. We conduct extensive experiments from real-world sample collections and demonstrate that our developed system outperforms multiple other existing malware detection techniques.
The ever-growing interest witnessed in the acquisition and development of unmanned aerial vehicles (UAVs), commonly known as drones in the past few years, has brought generation of a very promising and effective technology. Because of their characteristic of small size and fast deployment, UAVs have shown their effectiveness in collecting data over unreachable areas and restricted coverage zones. Moreover, their flexible-defined capacity enables them to collect information with a very high level of detail, leading to high resolution images. UAVs mainly served in military scenario. However, in the last decade, they have being broadly adopted in civilian applications as well. The task of aerial surveillance and situation awareness is usually completed by integrating intelligence, surveillance, observation, and navigation systems, all interacting in the same operational framework. To build this capability, UAV's are well suited tools that can be equipped with a wide variety of sensors, such as cameras or radars. Deep learning has been widely recognized as a prominent approach in different computer vision applications. Specifically, one-stage object detector and two-stage object detector are regarded as the most important two groups of Convolutional Neural Network based object detection methods. One-stage object detector could usually outperform two-stage object detector in speed; however, it normally trails in detection accuracy, compared with two-stage object detectors. In this study, focal loss based RetinaNet, which works as one-stage object detector, is utilized to be able to well match the speed of regular one-stage detectors and also defeat two-stage detectors in accuracy, for UAV based object detection. State-of-the-art performance result has been showed on the UAV captured image dataset-Stanford Drone Dataset (SDD).
We introduce an algorithmic method for population anomaly detection based on gaussianization through an adversarial autoencoder. This method is applicable to detection of `soft' anomalies in arbitrarily distributed highly-dimensional data. A soft, or population, anomaly is characterized by a shift in the distribution of the data set, where certain elements appear with higher probability than anticipated. Such anomalies must be detected by considering a sufficiently large sample set rather than a single sample. Applications include, but not limited to, payment fraud trends, data exfiltration, disease clusters and epidemics, and social unrests. We evaluate the method on several domains and obtain both quantitative results and qualitative insights.